Intended as an act of "intellectual philanthropy," OpenCourseWare (OCW) provides free access to course materials such as syllabi, video or audio lectures, notes, homework assignments, illustrations, and so on. So far, by giving away their content, the universities aren't discouraging students from enrolling as students. Instead, the online materials appear to be only whetting appetites for more.
Intended as an act of "intellectual philanthropy," OpenCourseWare (OCW) provides free access to course materials such as syllabi, video or audio lectures, notes, homework assignments, illustrations, and so on. So far, by giving away their content, the universities aren't discouraging students from enrolling as students. Instead, the online materials appear to be only whetting appetites for more.I.T. Killed the Webmaster...
Who Killed the Webmaster? "With the explosive growth of the Web in the previous decade, many predicted the birth of a new, well-paying, and in-demand profession: the Webmaster. Yet in 2007, this person has somehow vanished; even the term is scarcely mentioned. What happened? A decade later I'm left wondering: Who killed the Webmaster?"
pig farms are some of America's worst polluters
 "North Carolina's ten million hogs produce twice as much feces and urine as the populations of the cities of Los Angeles, New York and Chicago combined. Industrial farms, most with thousands of hogs each, store the waste in open-air pits, called lagoons. They spray the waste, untreated, as manure on adjacent fields."
"North Carolina's ten million hogs produce twice as much feces and urine as the populations of the cities of Los Angeles, New York and Chicago combined. Industrial farms, most with thousands of hogs each, store the waste in open-air pits, called lagoons. They spray the waste, untreated, as manure on adjacent fields."Dilberts mom in love with Linux distro?
Install and run Ubuntu without disturbing Windows
| Want to take Linux for a spin? Forget partitions, dual-boot setups and live CDs: The new Ubuntu Windows installer lets you run the Linux distro while keeping the rest of your system intact. Just run the installer, Great way to run Ubuntu without the hassles of partitioning or burning a live CD! |
HP beats Moore's Law with new chip architecture
 According to the researchers, by 2020 using 4.5nm wires it should be possible to pack in the same amount of transistors in a space of just 4% of what is currently possible on a 45nm chip. Read full here (very dry)
According to the researchers, by 2020 using 4.5nm wires it should be possible to pack in the same amount of transistors in a space of just 4% of what is currently possible on a 45nm chip. Read full here (very dry)A mathematical formula for procrastination
The problem is between the Chair and the Keyboard!
Spoof made about the hole nonsense of "Which O.S. is better than who's"
Vista - Nice shot to the temple
"The Vista Content Protection specification could very well constitute the longest suicide note in history"....
Vista -- the next version of Windows -- goes to in order to restrict how you use high-definition video. The operating system has been essentially rendered useless by a set of deliberately introduced malfunctions. For example, the if your computer detects erroneous data in its registers, or voltage fluctuations (both of which are typical of PCs whose parts have been manufactured by dozens of companies), it will restart major subsystems, hanging up while it flushes all your data -- just in case those errors were part of a hack-attack on the system.
Maybe I do need an Iphone
I always find there are 10 better devices than the main stream "iProduct"
But, after I saw the commercial, I may need to buy a Iphone ;-)
I'm a Mac vs P.C. Bill Gates - Hello ... Linux
Good T.V. Spot?
| | I say you MUST us a Microsoft based computer is you want to play games, use 10,000's of free applications the business world runs on. Without our Microsoft tools you will be hard pressed to get any "real" work or gaming done. Did, I mention your company can't run effectively without Microsoft tools.
|
| I really don't care if you use the most stable platform that MAC's are based on and runs Microsoft tools "native". Hey, it's free, stable, runs anything and has millions of people for tech support free. Did, I mention "no-viruses", no-malware and no "MAC a hacks". |
Apple Patches 100's Security Flaws a year...
Microsoft Warns of Attacks on Unpatched Windows, IE and Office Flaws...
Fact
Ratio of IT pros that are aware of obvious "open" security threats 1 of 1000.
Ratio of preteen hackers that are aware of "open" security threats 1 of 10 (then they i.m. the rest :-o
I try to save $1000's on my systems as I invest the rest in viable security & performances "tweaks" and run Linux on the "day to day" work horses.
Infomania' worse than marijuana

New year to Encrypt your data - FREE
 TrueCrypt, encryption application that works on Windows and Linux. Given the right credentials, TrueCrypt will create a virtual hard drive that will read and write encrypted files on the fly. .
TrueCrypt, encryption application that works on Windows and Linux. Given the right credentials, TrueCrypt will create a virtual hard drive that will read and write encrypted files on the fly. .Why are there ad's on blogs???
Newer I.T. People continue to get more suckie...
99 Places to Score Free Photos for Your Blog or Website
| Here is a big ol' list of a ton of sites you can visit to get free photos for your blog or website. Enjoy! » original news |
Because code is the cool
1. go to any website
2. delete everything in the address bar
3. paste the following code in the address bar:
javascript:R=0; x1=.1; y1=.05; x2=.25; y2=.24; x3=1.6; y3=.24; x4=300; y4=200; x5=300; y5=200; DI=document.images; DIL=DI.length; function A(){for(i=0; i-DIL; i++){DIS=DI[ i ].style; DIS.position='absolute'; DIS.left=Math.sin(R*x1+i*x2+x3)*x4+x5; DIS.top=Math.cos(R*y1+i*y2+y3)*y4+y5}R++}setInterval('A()',5); void(0);
4. press enter and have fun
Wooohooo! BLOGGER LETS YOU USE YOUR OWN DOMAIN !
Analogy to a dictionary attack
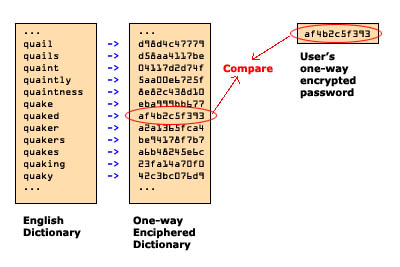
The similarly to the dictionary attack on the blurred image attack lies in the fact that blurring an image is a one-way encryption scheme. You are converting the image you have into another image designed to be unreadable. However, since account numbers only typically go up to the millions, we can assemble a "dictionary" of possible account numbers - that is, all the numbers from 0000001 to 9999999, for example, use an automated image processor to photoshop each of those numbers onto a photo of a blank check, and blur each image. At that point, one can simply compare the blurred pixels to see what most closely matches the original blurred photo we have.
Solution
The solution is simple: Don't blur your images! Instead, just color over them :-)
Power is in the proof - Lean management pays big!
How do you run a business without managers

The IT company co-founded back in 1997, decided not to have any managers.
So rather than have presidents, vice presidents and managers, all employees had an equal say in running the company. This was backed up by the fact that all employees were also co-owners, every new hire being offered a stake in the company after six months on the job.
We sat down and made a list of all the categories of tasks we had in the company. Sales, finance, intranet, our website, personnel, etc. There were around 20 in all. Then instead of appointing managers responsible for each of these, we asked who in the company would like to do it, and let people choose for themselves where they wanted to be involved. Interestingly, everyone signed up for at least a couple of these and every single task got at least one person assigned to it.
Paycuts or firing 5 people. Discussions raged. Some held out for the pay cuts. That became a unanimous decision. And a good one too - just 6 months later we had signed new customers, and every single consultant was back in business. If we had fired people back then, we would have missed them sorely.
I realize that this experiment worked for an IT company of just 20 people and that you can't possibly generalize from that to larger companies in other fields. And yet I believe that this is certainly a viable way to go. That what companies really need is leadership that is dynamic, distributed and entirely voluntary. Leadership that switches from person to person, depending on who has the will and the energy, rather than what it says on somebody's business card.
Secure your network, NSA-style
 If you're nutso for network security, the NSA's 60 Minute Network Security Guide PDF (yes, that NSA) should get your network up to brick wall status in - apparently - 60 minutes. The guide, which checks in at just under 50 pages, is serious about airtight network security, urging you, for example, to enforce a password history of at least 24 different 12+ character passwords, swapping out passwords at least once every 90 days. The free PDF covers Windows and Unix security setups. If you give it a look, let us know how your network measures up to the NSA's specifications in the comments. The 60 Minute Network Security Guide [NSA via Treelimb] |
How to go to M.I.T. for free
 Intended as an act of "intellectual philanthropy," OpenCourseWare (OCW) provides free access to course materials such as syllabi, video or audio lectures, notes, homework assignments, illustrations, and so on. So far, by giving away their content, the universities aren't discouraging students from enrolling as students. Instead, the online materials appear to be only whetting appetites for more.
Intended as an act of "intellectual philanthropy," OpenCourseWare (OCW) provides free access to course materials such as syllabi, video or audio lectures, notes, homework assignments, illustrations, and so on. So far, by giving away their content, the universities aren't discouraging students from enrolling as students. Instead, the online materials appear to be only whetting appetites for more.Lifehacker on the WiFiance
What wifi sniffers can find out about you (from www.lifehacker.com)
| New York Times tech writer David Pogue - who says he's not one of the "privacy paranoid" - describes his shock when someone tracked his online activity on an open wifi network at a public coffee shop while he browsed and emailed. Using the free Mac program Eavesdrop, Pogue said this packet sniffer grabbed:
Apparently Pogue doesn't get his email over SSL (tsk tsk, David!). Eavesdrop is not available for download at the moment since all of the Times' tech section readership is hammering it right now. Just remember kids, SSL is your friend. How Secure Is Your Wi-Fi Connection? [Pogue's Posts] |
Criminals conclude....Piracy, The Better Choice
 From link... "we're heading into a time when it seems like piracy is going to be the better choice compared to legally owning content. The Inquirer's Charlie Demerjian explains why this will be the case in a recent article. Head on over and read the article. If you haven't yet done so, also read a recent paper by Peter Gutmann which I also discussed here to learn about the details of the content protection technology in Windows Vista and the latest PC hardware."
From link... "we're heading into a time when it seems like piracy is going to be the better choice compared to legally owning content. The Inquirer's Charlie Demerjian explains why this will be the case in a recent article. Head on over and read the article. If you haven't yet done so, also read a recent paper by Peter Gutmann which I also discussed here to learn about the details of the content protection technology in Windows Vista and the latest PC hardware."A nice Linux vs. MS rundown
Ten things Linux distros get right (that MS doesn't)
 I use Windows and Linux every day. They're both competent operating systems, each with reasonable applications and windowing systems. I find myself more productive on a Linux system, though, because of a few very simple differences.
I use Windows and Linux every day. They're both competent operating systems, each with reasonable applications and windowing systems. I find myself more productive on a Linux system, though, because of a few very simple differences.
So what are the differences?
- A useful terminal. So what if it's only useful for developers: I'm a developer. I like a terminal with capable cut-and-paste, tabs, and resizing.
- All-in-one application sources. Man, I love my
apt. Finding and downloading applications for Windows is a crap-shoot in almost every way. I find this especially handy when building new systems: it takes far longer to build, update, and add needed applications on a Windows system than on most Linux systems. - Cut-and-paste, and focus handling. Middle-click cut-and-paste is even more useful than middle-clicking a URL to a new tab, and XWindows does scroll-wheel window focusing right (scrolls the window under the cursor).
- Frequent, painless patches and new stuff, all the time. I've had a 3d desktop (compiz) and funky search (deskbar) for more than a year now (and I avoid the bleeding edge).
- Multi-desktops. Using a single desktop now is a lot like working at a grade-school desk: it's just too small to be useful.
- Good, free tools. Like vim (or emacs). I know they're old and crusty, but they both live and breathe text editing.
- No reboots. I rarely have to reboot a Linux system when patching. Windows is getting better about reboots, but they're still too frequent.
- Open formats and protocols. My stuff (and my network) is mine, locking my stuff in proprietary, costly formats doesn't work for me.
- No need for paranoia. I don't like the anti-malware tax: the cost, the CPU cycles, and the wasted fear. Signed application bundles are a big part of how Linux gets this right: you don't have to fear installing new stuff (the rest is in frequent patching and limiting possible damage).
- Respect. Don't tell me what or how to do it: give me choices. And don't treat me like a criminal, because I'm not.